Sub-prefix hijacking 4) Sub-prefix and its AS Hijack: In this scenario,... | Download Scientific Diagram

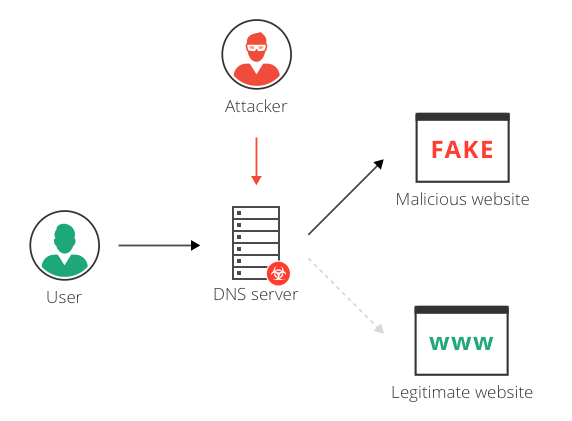
a) Standard configuration: the router acts as a proxy for DNS queries,... | Download Scientific Diagram

Unknown suspects hijacking our WiFi. Caught their MAC addresses - Information Security Stack Exchange

These random IPv6 dns addresses keep showing in my routers DNS server. It's basically “hijacking” my Windows Server domain controller as so clients cant reach it. Any advice on how to get











/img_04.png?width=873&name=img_04.png)